I often wonder how business managed to operate as efficiently without the IoT (internet of things). Access to the web, email, shared server files and electronic payments have certainly brought the digital revolution into everyday business practice. However, where there is gain there is also pain. The digital era not only revolutionised the way we conduct business, but it also reshaped the scope of business threats and the landscaped new paths for criminal activity.
As a business executive, consider how many emails, containing confidential information, your workforce send daily. Add to that invoices baring company details, electronic payments for accounts and transfers of monies from accounts to accounts. If your business stores client and supplier information for debit orders, or any other billing requirements at all, you fall within in the scope of a cyber-criminal target.
A long-standing client, who wishes to remain anonymous, recently felt the burn of a well thought out Phishing scam.
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. The information is then used to access important accounts and can result in identity theft and financial loss (phishing.org)
Client X recently submitted an insurance claim for her written off car. All claim forms were completed on her business letterhead, signed and hand delivered as required. In a follow up mail, sent from her computer, Client X requested the claim be paid into her investment account. As per company protocol, any change in banking details requires the following verification:
- Bank statement reflecting account name, account number and ID
- Letterhead, in the name of the claimant, with their handwritten signature sent from a verified email address
All checks were made and verified. The claim was submitted on a Friday morning and the money released in the afternoon. A follow up mail was sent to the client verifying that the transfer had taken place and a request for client X, upon receiving the money, to confirm. On the Monday, Client X called to enquire about the status of the money transfer. The Insurer was stumped, and forensics were immediately called to investigate.
Unbeknownst to all parties, Client X’s email server had been hacked and a Cyber Criminal had been monitoring activity in wait for Client X (owner of a medium size business) to engage in a financial transaction. Using her email account, with full access to her personal files and identification, the Cyber Criminal assumed control of her identity, replicated verified bank statements and began siphoning money from her business transactions into a temporary account. The external forensics team stated that they too were shocked at the professionalism of this specific cyber criminal’s scheme. The team said that of late, they have been inundated with calls for help from SME’s who have lost hundreds of thousands to similar activity.
In discussion with a Director of a well-known Durban based SME, he expressed grave concern over the “uneasy and unnerving” feeling knowing of many local businesses who have recently been targeted. “We can’t blame our staff if they’ve followed company procedures and taken every precaution they can,” he added, “but I can’t help but think, how long until it’s my company’s turn?”
Although we can’t close the door to Cyber Fraud, we can certainly stand guard at the virtual gates by ensuring that robust cyber policies are put in place to protect our business and staff.
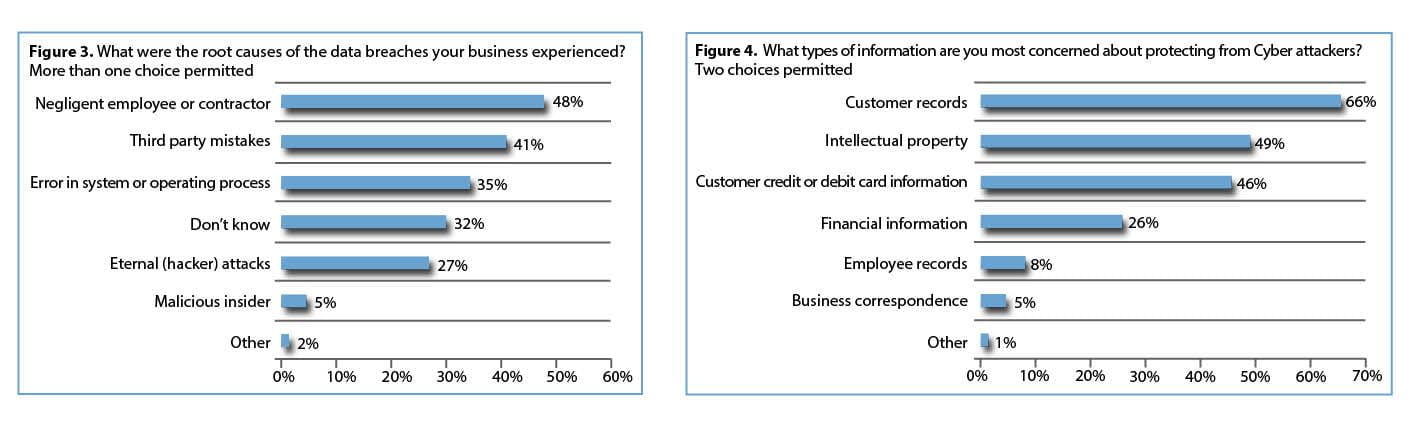
Fig 3 & 4: Small business cyber security attack statistics
https://smallbiztrends.com/2017/01/cyber-security-statistics-small-business.html
Our Cyber policy can protect in the following ways:
- Data breach incident response
Call our hotline for a pre-approved top breach response law firm, who will initiate an investigation and coordinate the response plan on your behalf. This hugely important support will guide you through the process of dealing with a cyber fraud of this nature.
- Cyber Crime/ Social Engineering Extension
This section of our product gives cover for our customer’s financial loss relating to a social engineering event such as phishing.
Don’t allow yourself to be the next victim.
Call SATIB Insurance Brokers Brokers to speak to a cyber insurance professional today.



